Posted by on November 11, 2012
Google's browser Chrome, version 23 was just released. We quickly installed it to our browser cloud. You can now cross-browser test your websites in this new browser.
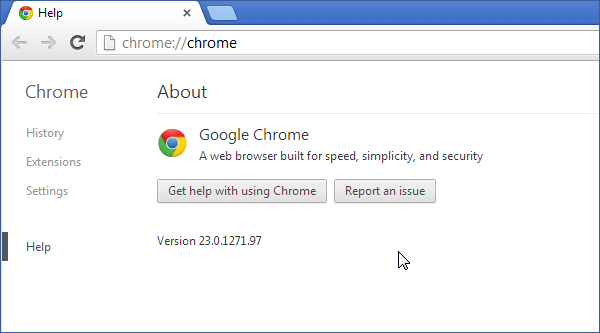
Try Chrome 23 in Browserling now!
What's new in Chrome 23?
- Added Do Not Track (DNT) setting.
- Hardware video acceleration is now 25% more power efficient.
- Added manager for site permission control.
- New icon for Chrome Web Store when opening new tab.
- On Mac OSX PPAPI Flash Player (or Pepper-based Flash Player) has been replaced the NPAPI Flash Player.
What's new for developers in Chrome 23?
- Added WebRTC - Real-time communication in the browser.
- Multimedia: Media Source Extensions - Allows appending data to an <audio>/<video> element.
- Multimedia: Track element - Add subtitles, captions, screen reader descriptions, chapters and other types of timed metadata to video and audio. Chrome currently supports the WebVTT format for track data.
- Pointer Lock (Mouse Lock) - Gives access to raw mouse movement, locks the target of mouse events to a single element, eliminates limits of how far mouse movement can go in a single direction, and removes the cursor from view. Obvious use cases are for first person or real time strategy games.
What security bugs were fixed in Chrome 23?
- CVE-2012-5115: Defend against wild writes in buggy graphics drivers. Credit to miaubiz.
- CVE-2012-5127: Integer overflow leading to out-of-bounds read in WebP handling. Credit to Phil Turnbull.
- CVE-2012-5120: Out-of-bounds array access in v8. Credit to Atte Kettunen of OUSPG.
- CVE-2012-5116: Use-after-free in SVG filter handling. Credit to miaubiz.
- CVE-2012-5118: Integer bounds check issue in GPU command buffers. Credit to miaubiz.
- CVE-2012-5121: Use-after-free in video layout. Credit to Atte Kettunen of OUSPG.
- CVE-2012-5117: Inappropriate load of SVG subresource in img context. Credit to Felix Grobert of the Google Security Team.
- CVE-2012-5119: Race condition in Pepper buffer handling. Credit to Fermin Serna of the Google Security Team.
- CVE-2012-5122: Bad cast in input handling. Credit to Google Chrome Security Team (Inferno).
- CVE-2012-5123: Out-of-bounds reads in Skia. Credit to Google Chrome Security Team (Inferno).
- CVE-2012-5124: Memory corruption in texture handling. Credit to Al Patrick of the Chromium development community.
- CVE-2012-5125: Use-after-free in extension tab handling. Credit to Alexander Potapenko of the Chromium development community.
- CVE-2012-5126: Use-after-free in plug-in placeholder handling. Credit to Google Chrome Security Team (Inferno).
- CVE-2012-5128: Bad write in v8. Credit to Google Chrome Security Team (Cris Neckar).
Happy cross-browser testing in Chrome 23!
Email this blog post to your friends or yourself!
Try Browserling!
Enter a URL to test, choose platform, browser and version, and you'll get a live interactive browser in 5 seconds!

 Subscribe to updates!
Subscribe to updates!
 BizSpark
BizSpark